Ransomware playbook (ITSM.00.099) – Canadian Centre for Cyber Security
Summary
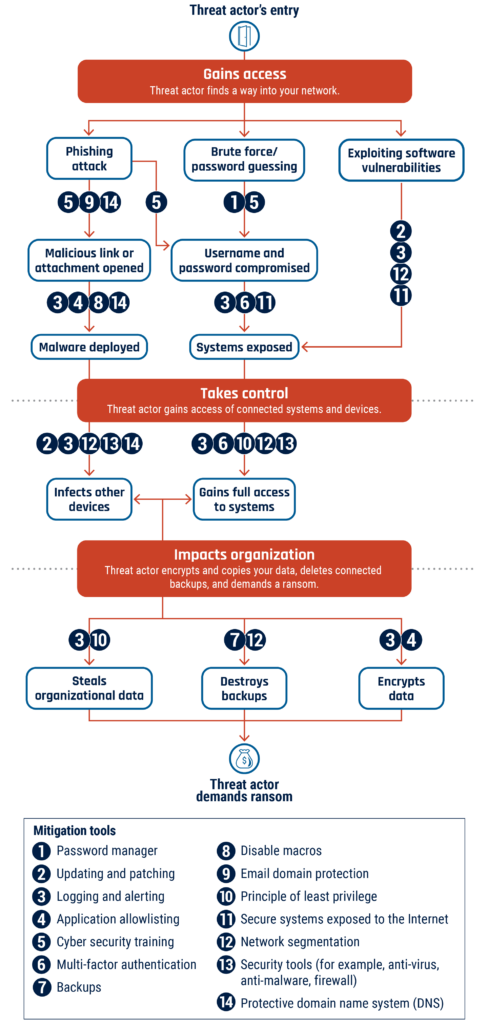
This official Canadian Centre for Cyber Security playbook explains how ransomware operates, why it has become a top cybercrime threat to Canada’s critical infrastructure, and what organisations should do before, during and after an incident. The guidance breaks into three practical sections: “Ransomware explained” (vectors, targets and tactics), “How to defend against cyber threats” (detailed security controls and planning) and “How to recover from ransomware incidents” (immediate response, recovery and lessons learned).
Key themes: ransomware now often involves data theft and extortion (double extortion), the rise of Ransomware-as-a-Service and Cybercrime-as-a-Service increases incident frequency, and agentic AI is accelerating both offensive capabilities and defensive automation. The playbook stresses defence-in-depth: offline backups (multiple copies), strong account and administrator controls, MFA, patching, segmentation, logging/alerting, application allow-lists and protected DNS. It also provides a four-phase incident response lifecycle (Prepare, Observe, Resolve, Understand) and an immediate response checklist (isolate systems, report to police/CAF Centre/Cyber Centre, assemble CIRT, change credentials, wipe and restore from clean backups).
Key Points
- Ransomware now frequently combines encryption with data theft and public extortion; double extortion is common.
- RaaS and CaaS lower skill barriers for attackers and have helped grow ransomware incidents (reported Canadian incidents rose ~26% p.a.).
- Agentic AI can make attacks autonomous, fast and adaptive — but can also enable faster automated detection and response; careful governance is essential.
- Defence-in-depth is mandatory: offline backups (2+ copies), regular testing, MFA, patching, network segmentation, logging/alerting and application allow-lists.
- Organisations must have documented and practised plans: backup plan, incident response plan (four phases), recovery plan and communications strategy; involve CIRT and external specialists where needed.
- Immediate actions on detection: isolate affected devices, change credentials (without locking out recovery), preserve evidence, report to law enforcement, Canadian Anti-Fraud Centre and the Cyber Centre.
Context and relevance
The playbook is timely for anyone responsible for IT, risk or business continuity. Ransomware is identified in the National Cyber Threat Assessment as the top cybercrime threat to critical infrastructure and remains a major risk for organisations of every size. Vendor concentration, cloud dependency and expanding AI/IoT surfaces increase exposure. Recovery costs reported in Canada doubled to CA$1.2 billion in 2023, underlining the financial and operational stakes. The guidance aligns with current trends (RaaS, double extortion, agentic AI) and provides concrete, practical controls and checklists to reduce risk and speed recovery.
Author style
Punchy and practical: this is not a high-level essay — it’s a pragmatic playbook. It tells you what to do, in what order, and why it matters. If you manage systems, backups, or incident response, the playbook contains actions you should implement and test now.
Why should I read this?
Short version: if you care about keeping your organisation running, skim the key points and implement the backups, MFA, patching and incident-play routines. This playbook saves you time by giving a tested checklist and clear recovery steps so you don’t have to guess under pressure.
Source
Source: https://cyber.gc.ca/en/guidance/ransomware-playbook-itsm00099