Defending against adversary-in-the-middle threats with phishing-resistant multi-factor authentication (ITSM.30.031) – Canadian Centre for Cyber Security
Summary
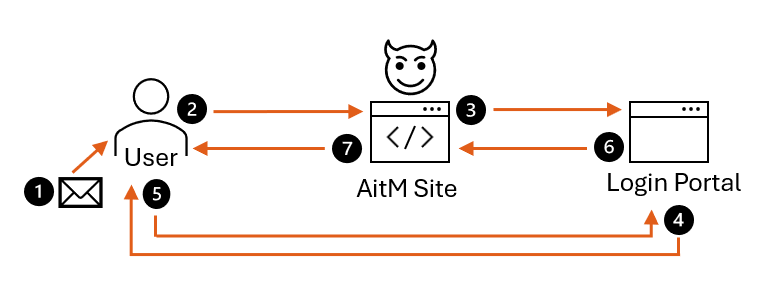
The Cyber Centre explains adversary-in-the-middle (AitM) phishing: attackers proxy users to legitimate login portals to capture usernames, passwords and MFA tokens. Proxy-based AitM kits hide the source of attacks by inserting multiple relays, making IP correlation ineffective. The Centre’s analysis of campaigns from 2023 to mid-2025 shows a clear shift from traditional AitM kits to proxy-based approaches, heavy use of business email compromise (BEC) and “living off trusted sites” (LOTS) techniques, and a high prevalence of campaigns leveraging compromised Canadian organisations.
The definitive mitigation is phishing-resistant multi-factor authentication (MFA) combined with conditional access policies (CAPs) such as registered device checks and strict IP restrictions. The report documents declining full-session compromises where phishing-resistant MFA and registered-device CAPs are widely adopted, and sets out practical recommendations for organisations, administrators and users.
Key Points
- AitM phishing proxies user sessions to steal credentials and MFA-verified sessions, enabling later account impersonation.
- Threat actors have largely shifted to proxy-based AitM kits that defeat IP-based detection by relaying traffic across multiple proxies.
- Most analysed campaigns (91%) used BEC/VEC tactics and 59% used LOTS, making detection harder because links originate from trusted services.
- Phishing-resistant MFA (FIDO2 security keys, passkeys, Windows Hello for Business) plus registered-device CAPs stop all known AitM techniques.
- Full-session compromises have fallen as organisations adopt phishing-resistant MFA and stricter CAPs, but many accounts remain unprotected.
- Immediate priorities: apply phishing-resistant MFA to all accounts (especially admins), remove weak fallback methods, restrict BYOD logins or route them through corporate VPN and tighten IP-based CAPs.
- User education remains important: verify unexpected file shares, double-check top-level domains, avoid unnecessary repeated logins and maintain good password hygiene.
Why should I read this?
Short version: if you care about keeping logins safe, this is essential. It shows how modern phishing tricks bypass old defences and why switching to phishing-resistant MFA and registered-device policies actually stops these attacks in their tracks. Quick fixes and user training help, but the real win is proper MFA and CAPs.
Author’s take
Punchy and simple: this isn’t theoretical. The Cyber Centre tracked hundreds of campaigns and found real impact on critical sectors. If you’re responsible for identity, zero excuses—prioritise phishing-resistant MFA now or expect more incidents and costly recoveries later.
Context and Relevance
This guidance matters because cloud adoption has moved the frontline from corporate networks to identity systems. Attackers exploit trusted services, compromised vendors and proxy kits to outrun email filters and IP-based detection. The report is directly relevant to IT, security and risk teams in government, critical infrastructure and any organisation that relies on cloud identity and single sign-on.
Adopting phishing-resistant MFA aligns with industry best practice and significantly reduces the likelihood of account takeover, data breaches and reputational damage. The guidance also provides operational actions: eliminate weak MFA fallbacks for administrators, secure BYOD sign-ins, enforce registered-device CAPs and maintain user training focused on BEC and LOTS threats.